How secure is the realm of connected cars?
The unique challenges preventing OEMs from filling these cyber security gaps with a definite set of security practices and countermeasures.
The boon of vehicle connectivity has also given birth to the bane of connected car hacking. With an average connected car’s go-to-market period being five years, both the physical and network security measures are often outdated by the time they are in production.
When was the last time you rerouted based on real-time traffic updates from navigation apps like Google Maps? Well, nowadays with the over-crowded traffic scene in India and also in developed markets the world over, we are almost mentally wired to do so. However, if you feel that’s not a connected car experience enough, you might be slightly further from the reality. Provided the fact we are not confusing connected cars with autonomous vehicles, let’s drive right into the highway of smart automobile experiences and investigate the needs and measures for ensuring their cybersecurity.
What is a connected car?
A ‘connected car’ is equipped with Internet access that may be shared inside the vehicle through a local wireless network. However, a car becomes ‘connected’ when it starts to consume data or access services from the cloud or starts to sync diagnostic data with the cloud. A connected car driver has continuous access to not only on-road information such as route and traffic congestion but also to multimedia content. The current crop of connected smartphone apps available in India such as Mercedes Me, BMW ConnectedDrive, Honda Connect, Toyota Connect, Ford SYNC, and Nissan Connect is continually adding features and allows car owners to be perpetually linked with their vehicles.
Fortified with features such as on-road assistance, vehicle diagnostics, geo-tracking, remote locking and temperature control, connected car owners certainly get a lot more out of their driving experience. As the average human’s daily schedule is being eased by robotic automation and artificial intelligence, the connected car is exponentially evolving every day from being a luxury to a necessity.
However, if appropriate security measures for this ‘soon-to-be-ubiquitous’ necessity are not mandated soon enough, the future of connected cars could be bleak. Would you believe that in some of the vehicles which debuted the connected features, it was possible for a hacker to disable the brakes and control the steering? Imagine this happening on a long ride with your beloved or family. Is this really possible? Can hackable connected cars be owned with trust?
How the heck is hacking possible?
There are three types of external communication networks in a connected car – Internet, WiFi and Dedicated Short-range Communication (DSRC). Hence to be specific, the boon of connectivity gives birth to this bane of connected car hacking. In 2018 itself, there have been 10 such hacks in the year’s first 10 weeks. Back in 2015, white-hat hacker duo Charlie Miller and Chris Valasek had demonstrated how evidently insecure today’s state-of-the-art connected cars are. Utilising a loophole in a Jeep Cherokee’s entertainment software, they had taken over dashboard functions, steering, brakes, and transmission of the vehicle while it was driving down the highway at 70mph/112kph.
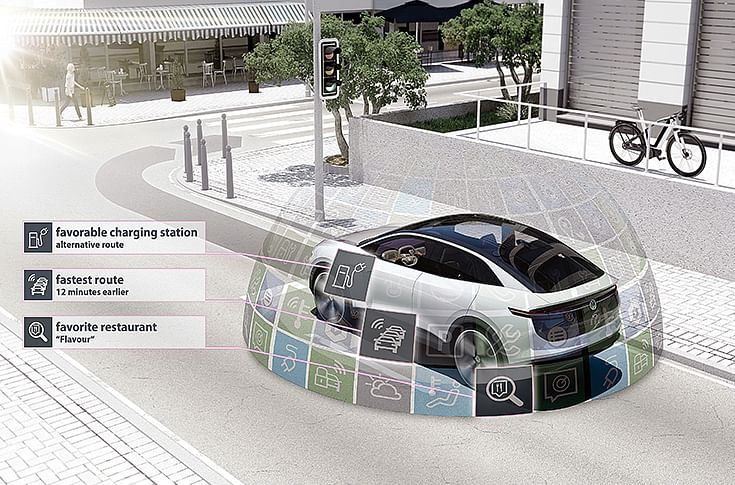
An intelligent, fully connected vehicle of the future: the Volkswagen ID Crozz show car concept.
Even in 2018, as the auto industry is cruising towards autonomous driving, unfortunately, connected cars are still prone to multiple cybersecurity flaws that lay out a red-carpet for hackers. These hackers sitting in distant corners of the globe are not just researchers, but also vary between cyber-criminals, competitors and hacktivists. Tapping into various security lapses and network flaws such as the Controller Area Network (CAN) Bus vulnerability, hackers target the Electronic Control Unit (ECU). For example, by intercepting the messages between the ECU and any of the subsystems from a digitally or physically compromised Onboard Diagnostics (OBD) port and injecting corrupt bits into multiple such communications (arbitrary CAN injections), it is possible to trick the ECU to perceive a subsystem as defective and take it out of the car network’s Intrusion Detection System (IDS).
Malware and digital exploits are getting complex by the day. However, with an average connected car’s go-to-market period being five years or more, both the physical and network security measures implemented at the time of design, are often outdated to by the time they are in production.
What’s holding the automobile industry back?
There are primarily two sets of unique challenges that are maiming the auto industry’s Original Equipment Manufacturers (OEM) from filling these cybersecurity gaps with a definite set of security practices and countermeasures.
Exponentially increasing electronic complexity: With leading-edge technological promises, the prospective connected car owners want more and more features to be crammed into the electro-mechanical ecosystem of the car. Such demands are forcing OEMs to multiply the average number of electronic vehicle nodes or ECUs of any car from 30 units of today to more than 100 in the next 3-5 years. Moreover, with each embedded unit necessitating its own operating software and hence millions of lines of code for operation and communications, even the foremost security measures are falling short of providing an overarching solution.
Multiplicity of stakeholders: With the characterising fragmentation of the automobile industry’s supply chain, there are too many players manufacturing components with their own standards and patch specifications.
As the multiple ECUs coming from multiple suppliers are integrated by the OEM to materialise certain features, the risks of cybersecurity flaws are further increased. Each component with its own cybersecurity needs may be protected at an individual level. However, when such components are integrated by the OEM using certain trademarked protocols, component customisation may create peculiar vulnerabilities unforeseen unless the components are integrated. Moreover, OEMs considering quality, innovation, cost and support as the criteria for choosing a supplier, don’t mandate the suppliers to raise the bars on their cybersecurity initiatives.
How do we control the hacks?
Every industry has its own set of drawbacks or challenges. Innovation or disruption stems from perceiving these challenges as opportunities and overcoming them with comprehensive ingenuity. To secure connected cars, there should be a multi-pronged approach.
From a network access perspective there should be:
- End-to-end security: Bi-directional authentication and end-point authorisation to ensure unique node identification and securing the communication techniques to factor out network snooping.
- User data protection: Ensure that all data going in and out of the vehicle is subject to various regulatory standards of privacy protection.
From a process perspective there should be:
- Well defined cybersecurity standards: Defined by the OEMs based on industry standards and best practices that are applied across its supply chain, covering the entire vehicular lifecycle.
- A well-defined incident management and recovery strategy that’s continually updated to boost applicability.
From a practice perspective there should be:
- Controlled access to firmware: With cryptographic key handling, digital signing techniques for firmware authorisation and secure boot to prevent any unidentified code from executing and modifying system internals.
- Physically disable or remove ports such as debug ports or serial ports through which privileged access to the hardware is possible.
- Using network and process isolation architecture to protect critical networked devices and use dedicated communication channels for safety critical sensors and devices to prevent spoofing.
- A rigorous anomaly detection system that identifies intrusions from unexpected variations or patterns of information exchange.
- Defining and implementing coding principles that ensure defensive programming practices and compliance with universal security standards.
As hackers keep the chase on and OEMs innovate to secure their products, within the coming decade itself the connected cars industry will undergo a sea-change in terms of security protocols and practices. Starting with the recent OEM-supplier alliances and end-user forums, the future certainly doesn’t seem disconnected.
ABOUT THE AUTHOR
Sherry C Kunjachan is the Strategic Initiatives Leader for Automotive Engineering Services at QuEST Global, which is a focused global engineering solutions provider and production engineering partner serving the product development & production engineering needs of high technology companies in the aero engines, aerospace and defense, automotive, oil and gas, power, medical devices, industrial and other high-tech industries.
(This article was first featured in the 1 June 2018 issue of Autocar Professional)
RELATED ARTICLES
Inside Mahindra Last Mile Mobility’s Rs 500 Crore Modular Platform Strategy
Mahindra Last Mile Mobility has launched the UDO, an electric three-wheeler built on a new Rs 500-crore modular platform...
How the India-EU Trade Deal Could Quietly Reshape the Auto Industry
While immediate price relief for the buyer is unlikely, the India-EU FTA will help reshape long-term industry strategy, ...
Policy, Protectionism and Pressure: Inside India’s Construction Equipment Downturn
India’s construction equipment sector faces a tough battle as it takes on cheaper imports from China and a slowdown in g...






 27 Jul 2018
27 Jul 2018
 6541 Views
6541 Views





 Shahkar Abidi
Shahkar Abidi


 Prerna Lidhoo
Prerna Lidhoo


